Risk Management & Real-Time Threat Detection
Security Intelligence and Analytics for HPE NonStop™ Integrity Servers.
XYGATE SecurityOne™ (XS1)
NonStop Security Analytics
XYGATE SecurityOne is a next-generation risk management and security analytics platform with all the necessary components to ensure your team is ready to face security threats. SecurityOne combines patented contextualization technology, real-time threat detection, integrity monitoring, compliance, privileged access management and much more, through a unified browser based dashboard – deployable on premise or in the cloud.
SecurityOne strengthens your team with real-time threat and compliance data to ensure they can respond to risks quickly all while saving time, increasing operational efficiency of your resources and maximizing the return on your security investment.
| XYGATE SecurityOne Packages What's Included |
Integrity Monitoring | Compliance | Suite+ |
| Meets PCI DSS 4.0 Requirements 10, 11, 12 |
Meets PCI DSS 4.0 Requirements 2, 5, 6, 8, 10, 11, 12 |
Meets PCI DSS 4.0 Requirements 1 - 12 |
|
| Real-time, intelligent file system and configuration integrity monitor |
 |
             |
             |
| Real-time compliance monitoring for PCI, GDPR, HPE Hardening Guide and more |
             |
             |
|
| Configuration & Compliance Monitoring for NonStop Appliances (console and CLIM) |
             |
||
| Patented Security Intelligence, Threat Detection, and Appliances |
             |
||
| Role-Based Access Control |
             |
||
| Privileged Access Management |
             |
||
| Keystroke Logging |
             |
||
| Dynamic Object Security |
             |
||
| Wildcard and Regex Protection for Resources and Objects |
             |
Threat Detection
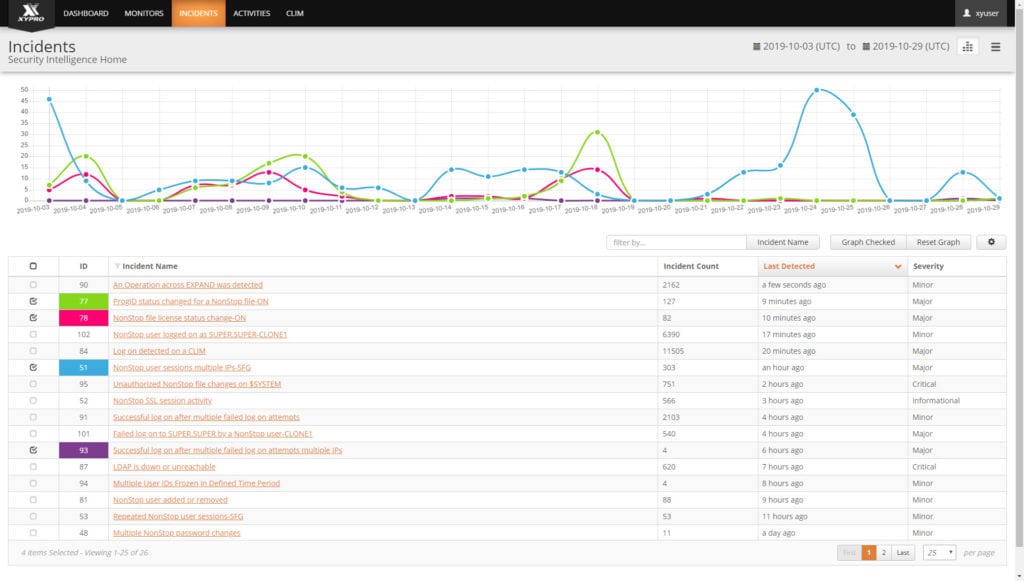
XYGATE SecurityOne® provides real-time Security Intelligence and Analytics for the HPE Integrity NonStop Server. XYGATE SecurityOne is designed to actively detect NonStop specific Indicators of Compromise and alert on suspicious activity. Using patented technology, XYGATE SecurityOne gathers data from multiple disparate NonStop server sources including application and system data, subsystems, user behavior, file operations, network data, command input and other sources and uses specialized security intelligence algorithms to correlate, contextualize and analyze events to paint a detailed security incident picture in real-time for the NonStop. This enables security operators to hone in on and detect security events before they culminate into an incident or breach.
Integrity Monitoring
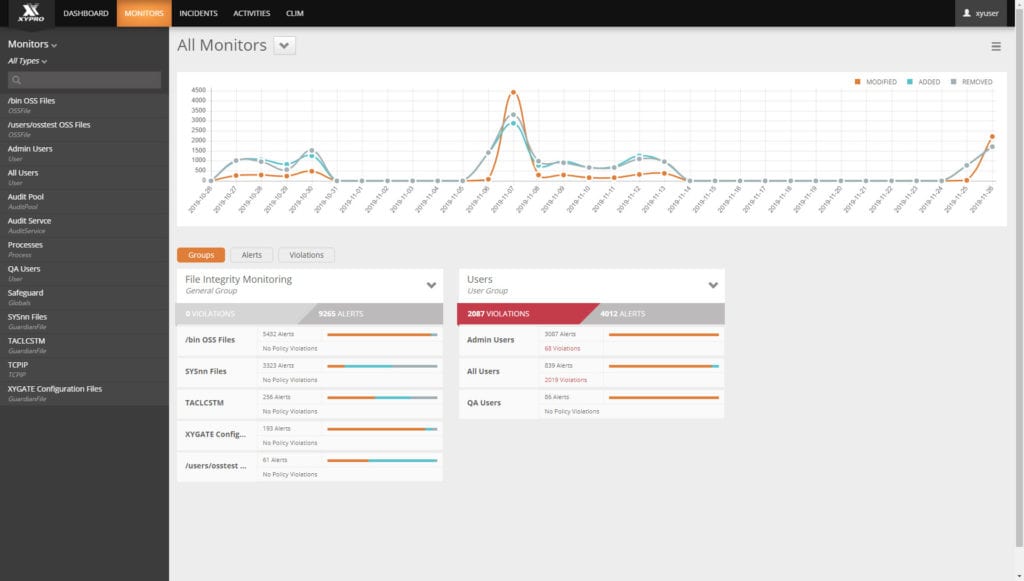

Attackers may attempt to overtake the operating system or application, steal or modify business-critical information or manipulate log files to hide malicious activity by targeting these files. Even authorized changes may result in misconfigurations, operator error or situations that expose the organization and data to increased risk of compromise. File and System Integrity monitoring identifies and alerts of any changes (create, modify, delete) to monitored systems and applications. Most regulatory compliance frameworks (PCI DSS, NERC CIP, FISMA, SOX, HIPAA, GLBA, ISO 17799 and more) require file and system integrity monitoring as a control for compliance. It is nearly impossible to achieve compliance without this control.
XYGATE SecurityOne provides real-time file and system integrity monitoring for HPE NonStop systems and workloads. SecurityOne alerts integrate with a wide range of enterprise security systems such your SIEM, SOAR or ticketing system.
Compliance
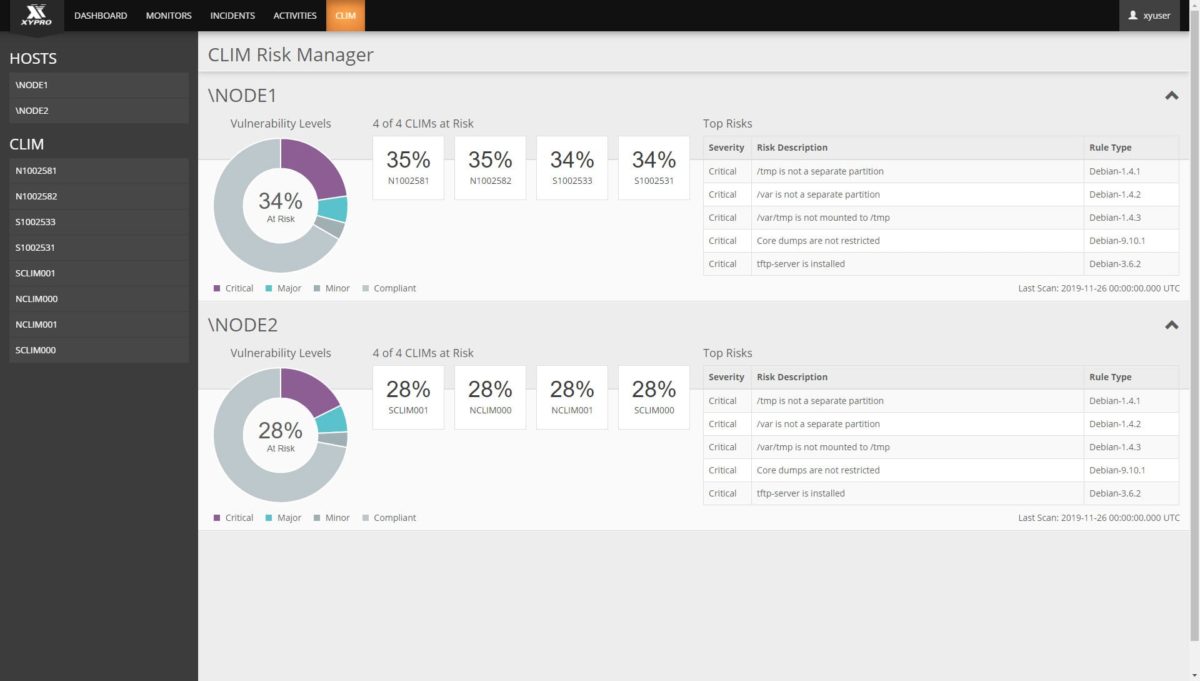
PCI DSS requires a network and system security status scan every 90 days. Businesses must identify and remediate all critical vulnerabilities detected during every scan. XYGATE SecurityOne compliance scanning is automated and risks are reported in real-time. This simplifies compliance activities and ensures the operational efficiency of your resources. SecurityOne provides easy to understand, detailed reports of your current and ongoing compliance status that are easily extended to other compliance frameworks such as GDPR, The HPE Hardening Guide and more. XS1 Compliance results are delivered through an easy to understand browser based dashboard for a comprehensive and continuous picture of your compliance status.
Appliance Sentry
Insecure and misconfigured appliances (or endpoints) like NonStop Cluster I/O Modules (CLIM) and NonStop Consoles (NSC) put your entire ecosystem at risk from external threats, data loss, and unauthorized access. Mitigating these risks is required for a secure environment. Different appliances CLIM and NSC security requires different tools to manage and enforce corporate policies. Monitoring these appliances has been largely a mystery or downright neglected because visibility into CLIM and NSC security has never existed – until now.
XYGATE SecurityOne – Appliance Sentry Module (ASM) continuously monitors your Appliances, identifies insecure or misconfigured settings and provides a risk score and remediation actions to ensure your appliances get to a healthy state and stay there.
Privileged Access Management
XYGATE Access Control (XAC), part of XYGATE SecurityOne, is the flexibility necessary to properly configuring system access. XAC is powerful, granular access control, for easy configuration of access according to users’ roles and responsibilities and to the right set of system resources.
Whether your organization chooses to very specifically define a job function down to individual sub-commands, or grant higher level access with fewer restrictions, XAC’s complete session and keystroke audits facilitates the creation and maintenance of this secure environment without compromising employee effectiveness and efficiency.
Object Security
XYGATE Object Security (XOS), part of XYGATE SecurityOne, is a comprehensive solution for securing all aspects of your NonStop system, covering both Guardian and OSS environments. XOS provides dynamic rules that can vary based on a variety of characteristics of each access attempt. Rules can change dynamically, based on who is requesting the access, the age of the file, the location of the requester and more. Imagine knowing you protection for objects that don’t yet exist! Remove your worry about whether everything is protected – it is.
XS1 dynamic access rules are applied to resource objects, such as volumes, subvolumes, files, devices, subdevices, processes and subprocesses and are critical for real-time threat detection and analytics.
If you’re looking to simplify Safeguard ACL sprawl, XOS eliminates complex ACL hierarchy, gives you wildcarding and regular expressions which can compress SG rules up to a 10:1 ratio. One XOS rule can cover tens or hundreds (or more) Safeguard ACLs. We have numerous customers go this route and never look back.